The digital transformation of the manufacturing sector, including concepts like Equipment-as-a-Service (EaaS), is reshaping how industrial machines are operated and maintained. Remote access and management have become prevalent — a trend further accelerated by the COVID-19 pandemic. Despite this, safety functionalities – particularly the reset after safety events (e.g., after a light curtain is triggered) – are still exclusively performed locally. This is a necessary safeguard, ensuring that a human operator verifies the absence of danger before resuming machine operation.
Given the increasing demand for remote operations, a natural question arises: can the reset of safety events (acknowledgement, ACK) be performed securely and safely from a remote location, over public networks?

Figure 1: Safety use case at a tooling machine; Orange: Danger zone, Yellow: Existing manual reset, and Blue: Remote acknowledgment.
Approach and Requirements
To address this question, we conducted a comprehensive requirements analysis via expert workshops with stakeholders from machine safety and OT security, complemented by an in-depth review of relevant standards and regulations. The aim was to establish a foundation for a solution that meets both safety and security objectives.
Key requirements were identified, including:
- Ensuring integrity and authenticity of all commands and video feeds, so that only authorized operators can perform a reset, and all actions are attributable.
- Assigning clear responsibilities to avoid conflicting actions or errors; each machine may only be controlled by one remote operator at a time.
- Guaranteeing that video feeds are unambiguously linked to the correct machine to prevent confusion or manipulation.
- Providing operators with sufficient situational awareness, including both live and historical video, to make informed decisions regarding safety.
- Disabling remote reset if decision-relevant information (such as video quality or recency) falls below acceptable thresholds.
- Ensuring flexibility in cryptographic mechanisms, with support for both conventional and post-quantum cryptography (PQC).
- Maintaining that remote resets do not reduce the safety level achieved by local procedures.
System Architecture and Concept
The solution is based on a secure gateway deployed within the production environment. This gateway connects local safety controllers and monitoring devices (such as cameras) to a remote operator, providing secure communication channels and enforcing access control policies.

Figure 2: Generalized Concept of the Demonstrator.
The main components and data flows are as follows:
- Monitoring: Cameras and safety sensors capture the state of the danger zone. All data is timestamped and cryptographically protected.
- Secure Gateway: Aggregates monitoring data, manages access, and secures communication between the production site and remote operator.
- Remote Operator Interface: Provides the authorized operator with access to live and historical video streams and status information. Only when all safety and security checks are satisfied, the system enables the operator to issue a remote acknowledgment.
A central server can be placed on the Internet to support external storage of video sequences, orchestrate operator authentication for multiple secure gateways at different sites, and facilitate connection establishment.
The acknowledgment is implemented as a two-step process to reduce the risk of accidental resets. The user interface design ensures that only the relevant machine’s video and data are displayed during the reset process.
Security and Safety Measures
The secure remote reset of safety events requires a holistic combination of safety and cybersecurity controls. In the following, we outline the key technical and organizational measures implemented to ensure that both safety and security objectives are consistently met throughout the system.
- End-to-End Data Protection: All communication, including video streams and remote commands, is protected using cryptographic measures. Live video is transmitted using mutually authenticated and encrypted channels (e.g., DTLS), while stored video sequences and commands are digitally signed and timestamped.
- Authentication and Authorization: A robust certificate-based system ensures that only authorized operators may perform resets, with granular control over operator-machine assignments.
- Auditability: All actions and data are logged for forensic analysis and compliance. Video sequences remain protected during storage and transmission.
- Trust Anchors and Crypto Agility: The system employs both software and hardware-based secure elements as trust anchors, supporting a range of cryptographic algorithms, including post-quantum schemes.
- System Hardening: The gateway is based on a hardened operating system (GyroidOS), with application isolation and full disk encryption. Additional measures such as control-flow integrity are used to further reduce the attack surface.
Implementation and Demonstrator
A proof-of-concept demonstrator was developed to validate the architecture. The testbed comprised a DOBOT MG 400 robot arm, danger zone monitoring using cameras and a light curtain, and a secure gateway with hardware-based trust anchors.
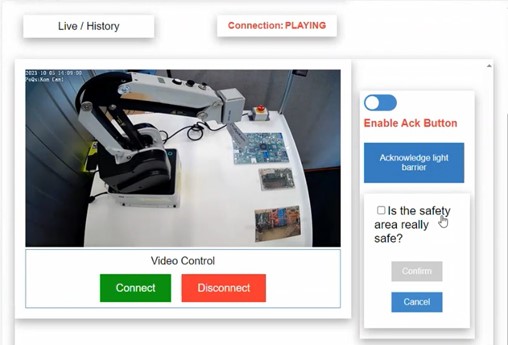
Figure 3: Remote operator panel to view the danger zone andsend a remote acknowledgment.
The remote operator panel, implemented as a web application, allows situational assessment and remote acknowledgment under controlled conditions. The system was evaluated with both traditional and post-quantum cryptographic algorithms, demonstrating its flexibility and readiness for future security requirements. Video and command data were transmitted and protected as specified, and the system reliably prevented remote resets when decision-relevant information was insufficient.
Project Context and Outlook
This work was carried out in the context of the “PoQsiKom” project, supported by the German Federal Ministry for Economic Affairs and Climate Action (BMWK). Our results demonstrate that secure remote acknowledgment of safety events is technically feasible without compromising safety.
Nevertheless, several challenges remain for future research. These include the efficient and scalable assurance of video authenticity, the direct integration of trust anchors into end devices, and the adaptation of the concept to other sectors with different specific requirements. Engagement with regulatory stakeholders will be essential before remote acknowledgment can be widely adopted in practice and standards.
Conclusion
Remote reset of safety events represents a significant step towards fully digitalized, flexible, and efficient manufacturing processes. Our work demonstrates how a secure gateway architecture, rigorous requirements engineering, cryptographic agility, and robust implementation can enable safe and compliant remote operation in safety-critical environments.
If you are developing similar solutions, securing industrial systems, or simply want to learn more – get in touch. For further technical details, please refer to the full paper: “Gateway to the Danger Zone: Secure and Authentic Remote Reset in Machine Safety”.
Authors

Nikolai Puch
Nikolai Puch is a research associate and penetration tester at Fraunhofer AISEC, as well as a PhD candidate at Technical University of Munich, with a focus on secure and usable solutions for tooling machines. His research specifically addresses security in additive manufacturing, and human-machine authentication.
Contact: nikolai.puch@aisec.fraunhofer.de

Sebastian N. Peters
Sebastian N. Peters has been an IT security researcher at Fraunhofer AISEC since 2021, after completing master’s degrees in electrical engineering and information technology and in economics at RWTH Aachen University. He is pursuing his PhD at the Technical University of Munich, focusing on industrial cybersecurity — particularly authentication, trust establishment, protocol security, and critical infrastructure.
Contact: sebastian.peters@aisec.fraunhofer.de








